Purpose:
The purpose of the Commitment to Security Statement is to provide Quantros clients and prospective clients with an objective description of the system’s boundaries and security commitments.
Policy/Statement:
Commitment to Security:
Health information is an important asset to our company and Quantros, along with its employees, is committed to protecting the integrity, privacy and security of confidential health information as required by law, professional ethics, and accreditation requirements.
Quantros acknowledges our duty and responsibility to protect the privacy and security of Individually Identifiable Health Information (“IIHI”) generally, and Protected Health Information (“PHI”) specifically, as defined in the HIPAA Privacy and Security Regulations, the HITECH Act and other applicable laws protecting the confidentiality of personal information, and under principles of general and professional ethics. We also acknowledge our duty and responsibility to support and facilitate the timely and unimpeded flow of health information for lawful and appropriate purposes.
Quantros is a business associate as defined by HIPAA. As an organization, we are committed to maintaining compliance with the HIPAA Privacy and Security Rules. All Quantros workforce members comply with the requirements of the HIPAA regulations with respect to privacy principles of minimum necessary use, security safeguards and controls, and accountability and oversight; and make reasonable efforts to limit use of and access to PHI within its systems.
Quantros has implemented appropriate privacy and security policies and procedures to meet, and in many instances, exceed, the HIPAA privacy and security standards for five (5) key areas outlined below:
I. ADMINISTRATIVE SAFEGUARDS
Quantros has implemented policies, practices and procedures to safeguard protected health information as defined in the HIPAA Regulations CFR 45 Section 164.308 including, but not limited to the following policies:
- Security Management Process
- Quantros has implemented policies and procedures including an annual Risk Analysis to identify potential risk and vulnerabilities to the confidentiality, integrity and availability of ePHI and remediate those risks as needed.
- Quantros has a comprehensive Risk Management Policy including routine internal and external security audits, use of third-party security experts and annual review of all security policies and procedures.
- Sanction Policy
- Quantros maintains a Sanction Policy as part of our corporate HIPAA Privacy and Security Policy Manual regarding workforce member conduct relative to a number of areas that impact PHI. The Sanction Policy highlights the potential range of penalties when a workforce member violates any of the policies. Workforce members are trained annually including the Sanction Policy.
- Information System Activity Review
- Quantros has implemented automated and continuous system monitoring that provides alerts and notification to services staff. This includes procedures to follow when a system alert occurs.
- Assigned Security Responsibility
- Quantros has identified a Chief Security Officer and Chief Privacy Officer. Additionally, Quantros has a Privacy and Security Committee responsible for the overall privacy and security at Quantros.
- Workforce Security
- Quantros workforce members have access to PHI based on their job function in order to minimize access to PHI. Employment at Quantros is subject to completion of a successful background check. Quantros has a termination policy and procedure in place to ensure that access to PHI is terminated upon a workforce members employment ends with the company.
- Information and Access Management
- Access to all resources is controlled by Access Control Lists (ACL). The level of access is based on the workforce member’s job description within the organization.
- Security Awareness and Training
- All Quantros workforce members are required to have HIPAA training upon hire and at least annually thereafter.
- Quantros utilizes the current version of Kaspersky Endpoint Security and Anti-Virus Enterprise Edition on all production, development and test servers and on all user workstations. This includes real time scanning and nightly and weekly scans for all files and folders contained on each computer. Anti-malware databases are configured to be updated every hour for new signatures that are being made available from Kaspersky Labs.
- Quantros requires the use of complex passwords.
- Quantros monitors all log-on attempts. Logs are reviewed monthly for unauthorized access.
- Security Incident Protection and Response
- Quantros maintains an Incident Reporting Mechanism in order to facilitate the reporting of potential security incidents and/or breaches. Quantros takes all suspected incidents seriously and will investigate all suspected incidents as quickly as possible.
- Contingency Plan
- Quantros maintains and extensive Data Back-up Plan which creates and maintains retrievable copies of PHI within application level clustering and replication, disk and tape backups, snapshots on storage devices and storage device replication.
- Quantros maintains a disaster recovery plan for recovery in the event of failure or disaster including all critical elements of the applications, snapshot technology in the event of major data corruption, backup databases for production data and an alternate site in the event the primary site goes down.
- Quantros maintains a Disaster recovery (DR) site.
- Quantros periodically tests contingency plans to verify procedural steps are valid and to provide updates to the procedures.
- All Quantros applications, including its elements such as the network, servers, storage and databases are equipped and operated at high-availability.
II. PHYSICAL SAFEGUARDS
Quantros hosts all its SaaS applications, including PHI data in dedicated spaces (or cages) in data centers on the West Coast and the East Coast. These are co-location facilities or dedicated spaces in these Tier III/IV datacenters.
All security policies are set by the hosting facility. Quantros has reviewed these policies and verified acceptability. The data centers are SSAE-16 and SAS 70 certified. They maintain 24/7 manned security. All doors have alarm contacts, the building has ballistic entrances/bulletproof glass and no signage. Only authorized employees have badges that will get them in any door. The physical security requires both a proximity badge and a palm print biometric authentication be performed before anyone can gain access to the facility via man traps. The data centers have recording cameras spread throughout and outside the facility and several motion sensor lights.
Aside from the aforementioned facility security implementations, Quantros also has procedures and practices related to the following:
- Facility Access Controls
- Quantros has policies that allow for appropriate access to its data centers in support of restoration of lost data or under the disaster recovery plan. Additionally, Quantros has implemented a comprehensive Facility Security Plan for all of its locations, including data centers. This includes the physical security of the facilities and appropriate access to those facilities.
- Workstation Security
- Quantros has implemented policies and procedures that govern the use and security of workforce member workstations, including laptops and portable devices. This includes the encryption of all workstations and laptops.
- Device and Media Controls
- Quantros has implemented policies and procedures that govern the movement of all devices and media. This includes disposal (Hardware Sanitation Policy), re-use, data back-up, and data storage.
III. TECHNICAL SAFEGUARDS
Quantros has implement policies and procedures in order to meet the all the required and addressable specifications as defined in the HIPAA Regulations CFR 45 Section 164.312 Security Standard Technical Safeguards. These policies and procedures include:
- Access Control
- Unique user IDs and secure passwords for access to systems
- Automatic Logoff procedures
- Emergency Access procedures
- Data that is moving is encrypted using Secure Socket Layer and Transport Layer Security (SSL/TLS). Data at rest is either encrypted or de-identified.
- Audit Control
- All interactively and remote access to servers, network and storage equipment is logged on a Security Information and Event Management (SEIM) System. Database access and activities are also logged locally and centrally. All web accesses to the applications from users are logged in a platform and/or application specific database down to the activity level.
- Integrity Control
- Digital Signatures and Message Digest are employed to protect data from improper alteration or destruction during transit.
- Person or Entity Authentication
- User authentication is handled within the application. It is equipped with configurable options to comply with commonly enforced password policies in the market.
- Transmission Security
- Quantros’ applications are equipped with transmission security and data integrity mechanisms to protect the exchanges of Protected Health Information according to the Encryption Policy including SSL/TLS or SSH Encryption.
- Monitoring and Alerting
- Quantros uses several systems and tools that complement each other to provide the best protection and coverage for its hosted application environments. These include monitoring and alerting for the following:
- System and Services Health and Availability
- Resource Capacity and Utilization Monitors
- Application Performance Monitors
- Synthetic and Real User Monitors
- Quantros uses several systems and tools that complement each other to provide the best protection and coverage for its hosted application environments. These include monitoring and alerting for the following:
IV. ORGANIZATIONAL REQUIREMENTS
Quantros maintains Business Associate Agreements with all applicable customers and vendors. Business Associate Agreements are reviewed annually to ensure compliance with the latest requirements.
V. DOCUMENTATION REQUIREMENTS
Annual Assessments
Quantros has a comprehensive Compliance Audit Plan which includes a review of the following policies:
- Annual HIPAA Risk Assessment
- Annual review of all Privacy and Security Policies
- Annual review of Vendor Management Program
- Annual review of Disaster Recovery Plan
- Annual HIPAA employee training
Vendor Management Program
Quantros has an extensive Vendor Management Program in place to evaluate, select and monitor vendors in order to minimize the risks associated with vendors working with Sensitive Information. This program includes vendor screening, Business Associate Agreements, Service Level Agreements, and monitoring.
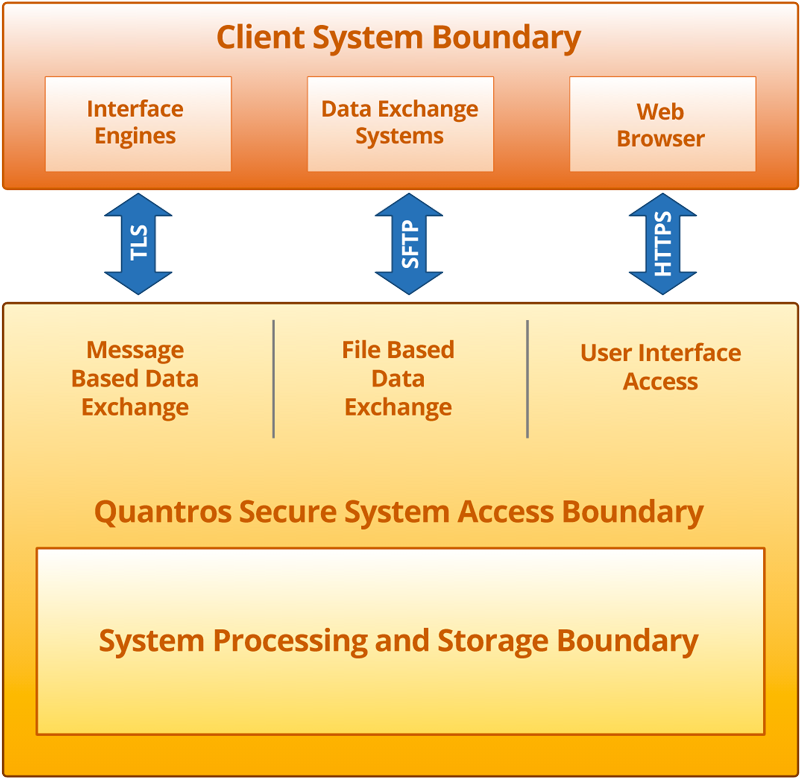
SYSTEM BOUNDARIES
The Client System Boundary illustrates data flow to and from Quantros and where data resided within Quantros’ enterprise.